March 6 / 2025 / Reading Time: 3 minutes
From Visitor Access to Total Compromise: A Bank Security Transformation
It began with a simple premise: what could an attacker accomplish starting from nothing more than a visitor's network connection? When a major banking institution engaged OSec to assess their security posture, they expected us to find a few configuration issues, perhaps some outdated software. What we discovered instead was a cascade of vulnerabilities that painted a sobering picture of how modern financial institutions can be compromised.
This is not just a story of vulnerabilities found and patched. It's a cautionary tale about how security assumptions, accumulated technical debt, and human factors can combine to create critical risks in even the most security-conscious organizations.
The Innocent Beginning: A Visitor's Perspective
Our assessment began in the bank's gleaming lobby, armed with nothing more than a laptop and the WiFi credentials freely given to visitors. This scenario mirrors exactly what any malicious actor could achieve—no special access, no insider knowledge, just the same starting point available to anyone walking through the front door.
Within hours, what started as routine reconnaissance evolved into something far more concerning. The visitor network, which should have been completely isolated from internal systems, revealed unexpected pathways into the bank's corporate infrastructure.

The Digital Met the Physical
As concerning as the digital vulnerabilities were, our physical security assessment revealed an equally troubling reality. Security, we discovered, is only as strong as its weakest link—and often, that link is human.
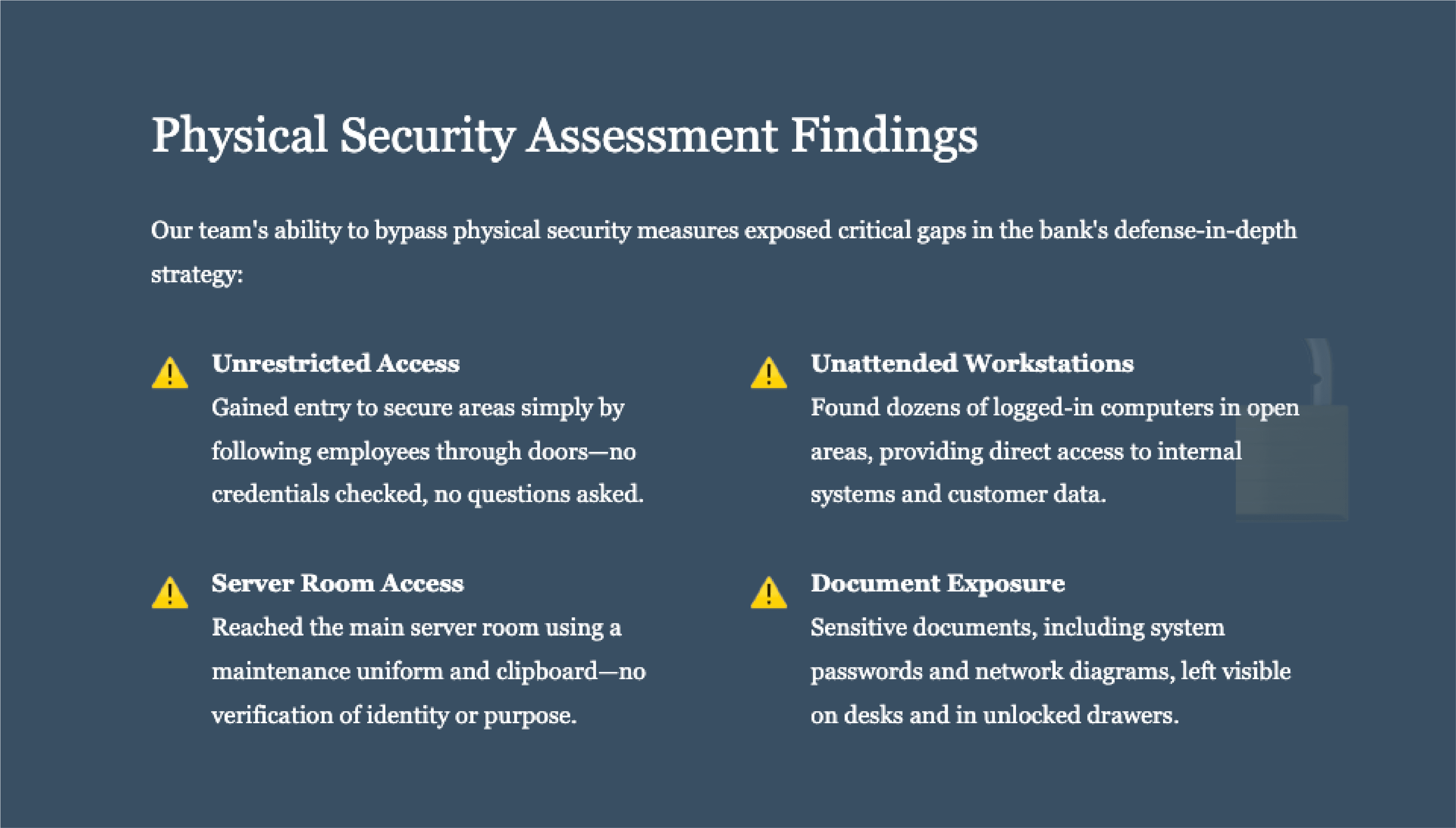
The most sophisticated digital defenses become meaningless when an attacker can simply walk in and sit down at an unlocked computer. - Internal Audit Lead
From Crisis to Catalyst: The Remediation Journey
Faced with these findings, the bank's leadership made a crucial decision: rather than implementing quick fixes, they would use this moment as a catalyst for comprehensive security transformation. What followed was a methodical, prioritized approach to rebuilding their security posture from the ground up.
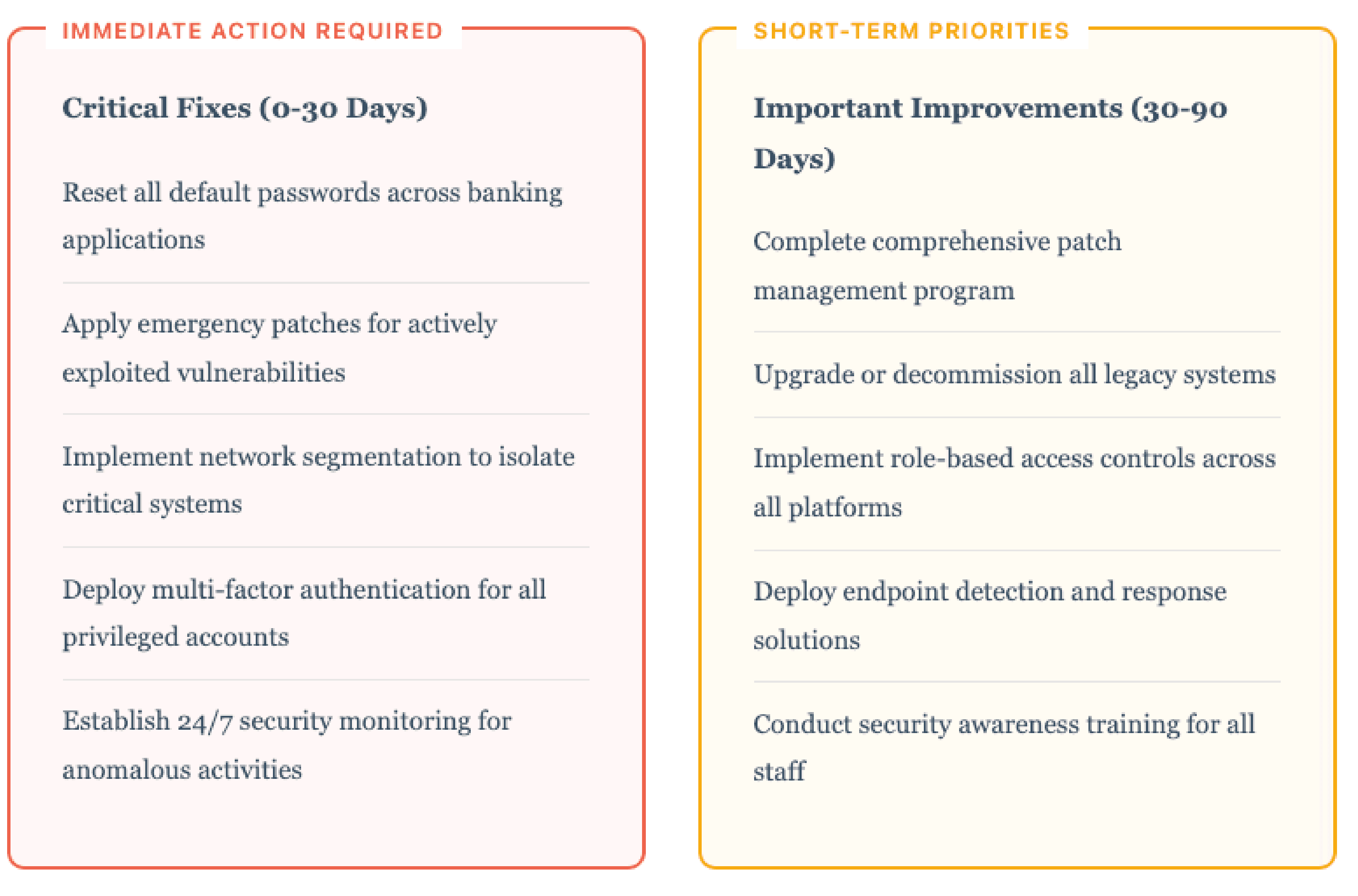
Strategic Prioritization: A Phased Approach
We worked with the bank to develop a remediation roadmap that balanced urgency with operational stability:
Measuring Success: The Transformation Impact
Six months after beginning the remediation process, the bank's security posture had undergone a remarkable transformation. The changes weren't just technical—they represented a fundamental shift in how the organization approached security.
Beyond Technology: Cultural Transformation
Perhaps the most significant change was cultural. Security evolved from being viewed as an IT concern to a shared responsibility across the organization. The bank implemented regular security awareness programs, turning every employee into a human firewall.
Physical security measures were completely overhauled, with biometric access controls, mandatory badge visibility, and a culture where challenging unknown individuals became not just acceptable but expected. The days of walking into secure areas with just confidence and a clipboard were definitively over.

A New Security Paradigm
Today, the bank stands as a model for how financial institutions can transform their security posture. Regular penetration tests now find only minor issues rather than critical vulnerabilities. More importantly, the organization has built resilience—the ability to detect, respond to, and recover from security incidents before they become breaches.
The journey from vulnerable to secure wasn't just about fixing problems; it was about fundamentally reimagining what security means in modern banking. By addressing both technological vulnerabilities and human factors, implementing defense in depth, and creating a culture of security awareness, the bank didn't just solve its immediate problems—it built a foundation for long-term security excellence.
For other financial institutions, the message is clear: comprehensive security assessments, while sometimes revealing uncomfortable truths, provide the roadmap for transformation. In an era where cyber threats grow more sophisticated daily, the question isn't whether you can afford to conduct such assessments—it's whether you can afford not to.
