Complete Attack Surface Coverage
Test everything that matters. From cloud infrastructure to APIs, web apps to network services - InCenter continuously validates your entire digital ecosystem.
Asset Class |
Testing Methodology |
Coverage Scope |
Frequency |
|---|---|---|---|
| Web Applications | Dynamic analysis, authenticated scanning, business logic testing | OWASP Top 10, API security, custom vulnerabilities | User Specified |
| APIs | Schema validation, authentication testing, rate limit analysis | REST, GraphQL, SOAP, gRPC endpoints | User Specified |
| Cloud Infrastructure | CSPM, workload scanning, IAM analysis | AWS, Azure, GCP, multi-cloud deployments | User Specified |
| Systems & Networks | Port scanning, service enumeration, configuration analysis | External perimeter, internal segments, cloud networks | User Specified |
| LLMs & AI | Prompt injection testing, model manipulation, data leakage | ChatGPT integrations, custom models, AI pipelines | User Specified |
| Mobile Applications | Static/dynamic analysis, API testing, local storage review | iOS, Android, hybrid applications | User Specified |
| OT/ICS | Passive monitoring, safe-mode testing, protocol analysis | SCADA, PLC, DCS, industrial protocols | User Specified |
Three Pillars of True CTEM
Complete Coverage
Map and monitor your entire attack surface across all environments
- Cloud, on-premise, hybrid infrastructure
- Web apps, mobile apps, APIs
- Network infrastructure & services
- Human attack vectors
- Third-party integrations
Continuous Validation
Prove actual exploitability with safe, real-world attack techniques
- Safe exploitation validation
- Attack chain analysis
- Adaptive testing scenarios
- Automated retesting
- Integration with security controls
Business Intelligence
Translate technical risk into financial impact and business priorities
- Financial impact modeling
- Business criticality scoring
- Industry-specific threat intelligence
- Executive reporting
- Compliance mapping
Your Security Stack Is Broken By Design
You didn't choose a fragmented security architecture. It chose you. Tool after tool, vendor after vendor, each solving a piece of the puzzle while the adversary sees the whole picture. We built one platform to rule them all.
Our CTEM Approach
Acronyms, sometimes that's all security seems to be about. CTEM is another one, and like so many its undefined. However, what we mean by it is clear - we will continuous uncover threat exposures (weaknesses/vulnerabilities that someone could use to harm your organization) and provide you a way to manage them effectively.
Most importantly, we believe one solution should cover your whole organization.
- How often do you want to test?
- How often do you have to test?
- How often can you test?
The answers to those questions will determine what continuous means to you and how often Incenter tests your environment.
Different testing schedules can be set for assets as and when needed.
If you conduct point in time assessments, or utilize a PTaaS approach - the system can mirror these, and provide far more.
How We Approach CTEM
Our methodology combines continuous automated validation with strategic human expertise to provide comprehensive threat exposure management.
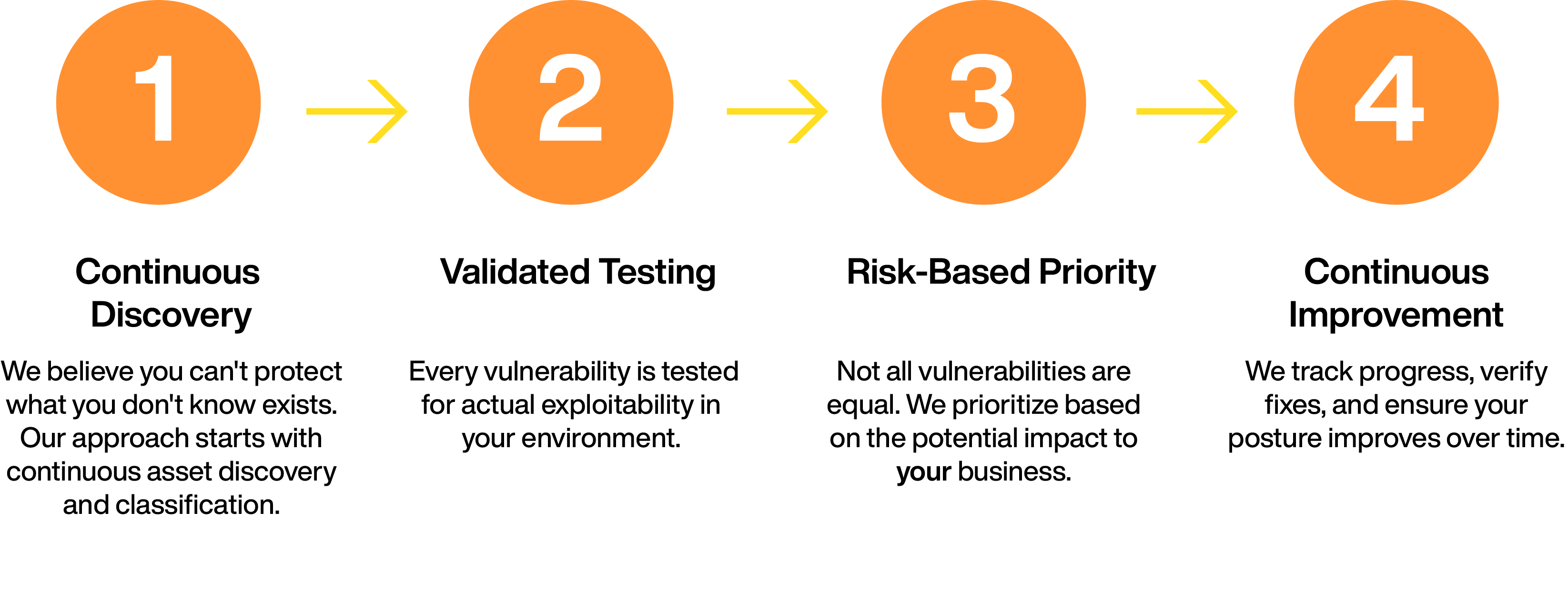
Our Testing Philosophy
Automation First, But Not Only
We believe in leveraging automation to handle the majority of tasks for continuous testing. Our autonomous systems:
- Run 24/7 without human intervention
- Validate thousands of potential vulnerabilities
- Adapt to infrastructure changes in real-time
- Eliminate false positives through validation
Human Expertise Where It Matters
Some attacks require creativity, business understanding, and adaptive thinking. We engage human experts for:
- Complex business logic flaws
- Multi-step attack chains
- Red team exercises with specific objectives
- Scenarios requiring social engineering
When Are Our Human Experts Triggered?
1. Complex Red Team Exercises: When you need to test specific attack scenarios or achieve trophy objectives that require adaptive thinking and creativity.
2. Complex Vulnerability Validation: When automated testing identifies potential vulnerabilities that require business context, multi-step exploitation, or manual verification.
Learn More: Why We Can't Automate Everything
Comprehensive Coverage Philosophy
We believe effective CTEM must cover your entire digital ecosystem. Our methodology addresses:
External Attack Surface
Everything an external attacker can see and target - from web applications to exposed services.
Internal Networks
Validation of segmentation, lateral movement paths, and insider threat scenarios.
Cloud Infrastructure
Multi-cloud environments with their unique attack vectors and configuration risks.
Human Factor
The people and processes that attackers often find easier to exploit than technology.
The Continuous Improvement Cycle
Our methodology is about driving measurable improvement.
- Baseline: Establish your current security posture
- Identify: Find and validate real exposures
- Prioritize: Focus on what matters most to your business
- Remediate: Fix issues with clear guidance
- Verify: Confirm fixes and prevent regression
- Measure: Track improvement over time
Compliance-Ready Reporting
Automated Attestation
One-click generation of compliance reports. Evidence collection happens continuously in the background.
Executive Dashboards
Real-time visibility into security posture with KPIs, risk trends, and breach probability calculations. Designed for board-level reporting.
Technical Documentation
Detailed remediation guidance with code examples, configuration changes, and validation steps. Export to ticketing systems automatically.

