June 11 / 2025 / Reading Time: 2 minutes
Executive Order Strengthens U.S. Cybersecurity
The cybersecurity landscape just shifted dramatically. With the signing of the new Executive Order on U.S. Cybersecurity, both government agencies and private companies face sweeping changes in how they protect their digital assets. From quantum-resistant encryption to automated IoT security monitoring, the requirements are both technical and transformative.
For organizations already stretched thin by evolving cyber threats, these mandates might seem overwhelming. Luckily these mandates have a mixed history of actually being enacted, but lets assume this will stick and break down whats important.
Why This Executive Order Matters Now
For the most part, previous cybersecurity policies often felt like checkbox exercises. They created bureaucratic hurdles without necessarily improving security. This new Order takes a different approach, focusing on practical measures that address real threats:

The policy removes outdated requirements and instead lets agencies focus on what actually works. It also clarifies that cyber sanctions should target only foreign malicious actors, taking a more nuanced approach to enforcement. Perhaps most importantly, it encourages decentralized decision-making at the department level—a refreshing change that reflects how security professionals actually think about protecting systems.
What Organizations Need to Do





Who Needs to Act (And How Quickly)
Federal Agencies
Decentralized decision-making means each department owns its security destiny—no more hiding behind central IT. Expect audits, expect scrutiny, and expect to move fast.
Financial Services
You're juggling existing regulations plus these new federal requirements. The good news? Many of the mandates align with what you're already doing. The challenge? Proving it with automated, continuous monitoring, and how much more is it going to cost?
Tech Companies and IoT Makers
Getting your devices certified under the new standards isn't optional.
Your 90-Day Action Plan
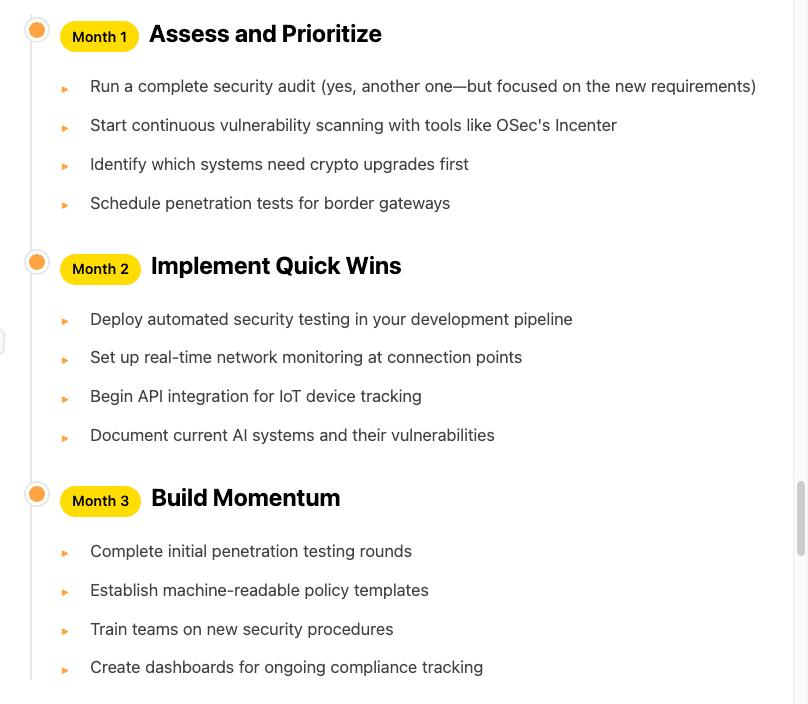
Looking Ahead: 6-12 Months
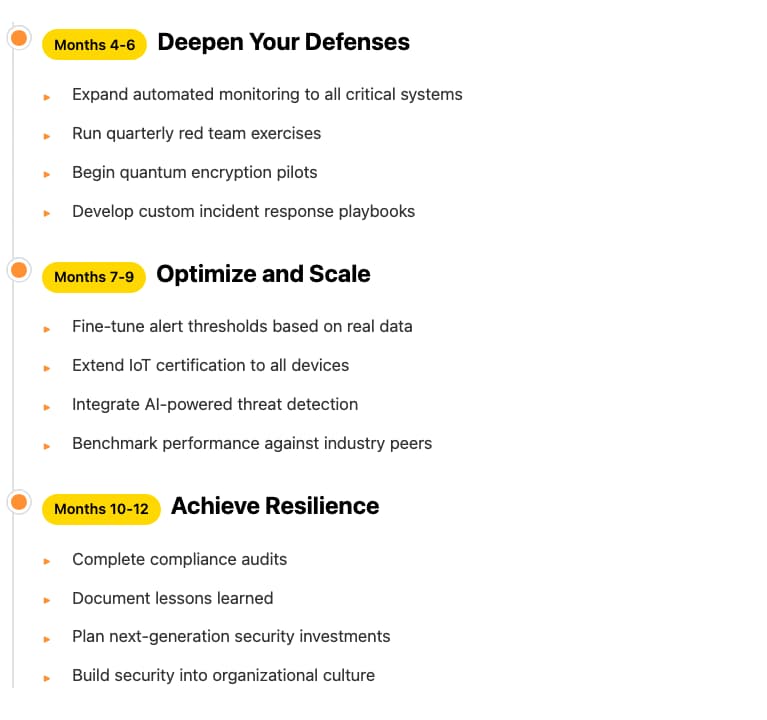
Why OSec Makes Sense
We provide:
- Real attack simulations, not checklist exercises
- Continuous testing that adapts as threats evolve
- Clear reporting that technical teams and executives can both understand
- API integration that works with your existing tools
- Expert support from people who've been in the trenches
We're not here to sell you a magic box that solves all your problems. Security doesn't work that way. Instead, we provide the testing, insights, and expertise you need to build genuine resilience.
Taking Action
The Executive Order isn't going away, and neither are the threats it addresses. Organizations that move quickly—investing in continuous testing, automated monitoring, and proactive defense—will thrive. Those that treat this as just another compliance exercise will struggle.
Start with an honest assessment of where you stand today. Then pick one area where you can make immediate progress. Maybe it's finally implementing continuous vulnerability scanning. Maybe it's scheduling that penetration test you've been putting off. Whatever you choose, start now.
The future of cybersecurity isn't about perfect defense—it's about continuous improvement, honest assessment, and staying one step ahead of evolving threats. With the right tools and mindset, the new requirements become an opportunity to build something genuinely secure.
______________________
Ready to see how OSec can help your organization meet these challenges?
Contact Us for a straightforward conversation about your security needs.
